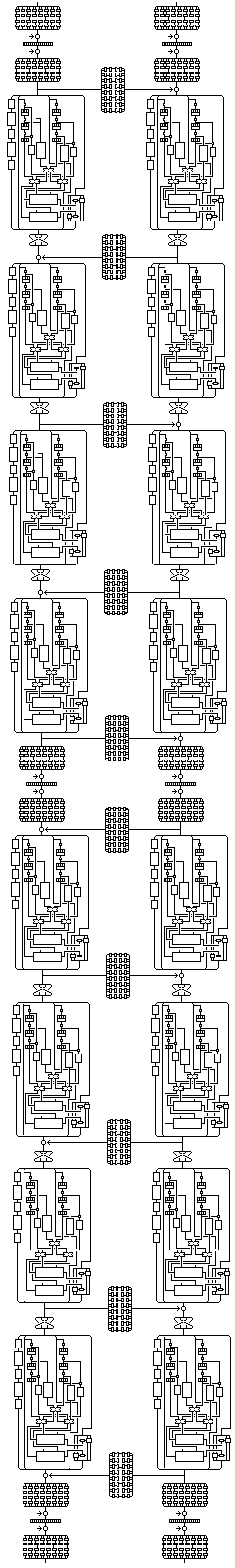
Quadibloc 2002B is a block cipher that operates on 256-bit blocks. It is built from components of the block ciphers Quadibloc 2002 and Quadibloc 2002A.
The diagram at left gives an overview of how it works. You may click on it to go to a larger version.
The overall structure of the cipher looks like this:
Q2002A Q2002A | | |---DIF--> XOR | | Q2002 Q2002 | | SBI SBI | | XOR <--DIF---| | | Q2002 Q2002 | | SBI SBI | | |---DIF--> XOR | | Q2002 Q2002 | | SBI SBI | | XOR <--DIF---| | | Q2002 Q2002 | | |---DIF--> XOR | | Q2002A Q2002A | | XOR <--DIF---| | | Q2002 Q2002 | | |---DIF--> XOR | | SBI SBI | | Q2002 Q2002 | | XOR <--DIF---| | | SBI SBI | | Q2002 Q2002 | | |---DIF--> XOR | | SBI SBI | | Q2002 Q2002 | | XOR <--DIF---| | | Q2002A Q2002A
The cipher proceeds as follows: the 256-bit block is divided into a right half and a left half. Both halves are independently subjected to one round of Quadibloc 2002A, followed by an extra diffusion phase. Then, the Quadibloc 2002A diffusion phase is also used as an f-function, by means of which the f-function of the left half is XORed with the right half. Each half is then separately subjected to four rounds of Quadibloc 2002; between rounds, after the interchange of subblocks, the Quadibloc 2002A diffusion phase is again used as an f-function in alternate directions. No interchange of subblocks happens after the fourth round, but the use of the diffusion phase as an f-function happens again. Then each half is again subjected to one round of Quadibloc 2002A, and again an f-function XOR between the two halves takes place. Four more rounds of Quadibloc 2002 are applied to each half, this time the f-function XOR is done before the interchange of subblocks (but the Quadibloc 2002 rounds are still encipherment rounds). After tha final Quadibloc 2002 rounds, no subblock interchange takes place, but the f-function XOR is performed, and finally each half undergoes another Quadibloc 2002A round.
The Quadibloc 2002 rounds are modified in one respect: instead of using S-boxes S1 and S2 inside the original Quadibloc f-function, S-boxes S5 and S6 are used. This is because the self-inverse S-box S1, derived from the original S1, remains used with the Quadibloc 2002A rounds and the Quadibloc 2002A diffusion phases used as an overall f-function, so it is desired not to use a related S-box for a different purpose.
Also, S8 and S9 as used in the Quadibloc 2002 rounds are referred to as S8 and S9, while in the Quadibloc 2002A rounds, S8A and S9A are used, and in the diffusion phases used as overall f-functions, S8B and S9B are used.
The basic method of generating keys used in Quadibloc XI and Quadibloc 2002 is used.
Subkeys are designated as follows: K1 through K7 are the 32-bit subkeys used in the first Quadibloc 2002 round applied to the left half, K8 through K14 are the ones used in the second Quadibloc 2002 round applied to the left half, and so on to K50 through K56 for the eighth Quadibloc 2002 round applied to the left half. K57 through K112 are the subkeys used for the right half. Similarly, SP1 through SP64 apply to the left half, and SP65 through SP128 apply to the right half.
The 128-bit subkeys used with the Quadibloc 2002A rounds are designated L1 through L12; again, L1 through L6 are the ones used with the left half, L7 through L12 the ones used with the right half, in order.
Subkey material is produced in the following sequence:
note that the subkeys for different parts of the cipher are interleaved with one another to an extent in this sequence.
The first variant of this cipher defined is Quadibloc 2002B FF (Full Feistel). In this variant, the diffusion phases from Quadibloc 2002A used as f-functions are replaced by a round of Quadibloc 2002A followed by an additional diffusion phase. The subkeys used for these ten f-functions are designated L13 through L32, and are generated immediately after L12. The rounds used as f-functions continue to use S8B and S9B rather than S8A and S9A, since for decipherment, the ones used as f-functions do not have their S-boxes interchanged as the ones used in line do.
The comments below raise a serious issue with the security of this design, and four additional variants are defined to address the issue.
Quadibloc 2002B ED (Extended Diffusion) is Quadibloc 2002B with the Quadibloc 2002A rounds replaced by Quadibloc 2002A ED rounds, so that each round modifies all four subblocks. The modification to the round of using S5 and S6 in place of S1 and S2 remains in place.
Quadibloc 2002B FE (Feistel/Extended) is Quadibloc 2002B FF using Quadibloc 2002A ED rounds, as above.
Quadibloc 2002B RF (Reduced Feistel) is Quadibloc 2002B FF with the six global Feistel operations occurring between pairs of Quadibloc 2002A rounds removed. Thus, only four global Feistel operations remain, and their subkeys will be L13 and L14, L15 and L16, L17 and L18, and L19 and L20 in order, and these subkeys will be generated immediately after L12, analogously with Quadibloc 2002B FF. The global Feistel operations preceding and following the central Quadibloc 2002A rounds will be reversed in direction, since an odd number of global Feistel operations are omitted preceding and following them.
Quadibloc 2002B RE (Reduced Extended) uses Quadibloc 2002A ED rounds (again, as modified), and uses six global Feistel operations, so their subkeys are now L13 through L24, by retaining, within each group of four consecutive Quadibloc 2002A rounds, the global Feistel operation after two of them. Note that this operation will be reversed in direction. On the other hand, the two operations preceding and following the central Quadibloc 2002A rounds will now be in their original direction.
This diagram may help to make clear which global Feistel rounds are retained in each variation, and their direction.

These variants, though, attempt to resolve the problem of information leakage around the Quadibloc 2002 rounds by reducing the number of global Feistel rounds, which reduces the coupling between the halves of the block. A more radical change is needed to solve the problem while not losing other strengths of the original cipher.
Thus, in Quadibloc 2002B DF (Disjoint Feistel) the same operations are used as in Quadibloc 2002B FF, but in a different order:
Of course, this still loses something, by not having different round types as closely interleaved.
As you might guess, Quadibloc 2002B FF corresponds more closely to my original conception of this cipher. The diagram I initially drew to illustrate the cipher, though, would have been too wide for that, so I decided to go with something more modest.
The complexity of this cipher certainly makes it look like the ne plus ultra for security. And yet, when I take another look at it, I see that this design could actually be seriously unsound.
After all, I entered into this design with the premise that Quadibloc 2002 was a very strong cipher, because of the profoundly nonlinear and inherently unanalyzable way in which its round modifies the fourth subblock, while Quadibloc 2002A was too similar to conventional, simple, and fast designs to be considered nearly as strong, even if it was quite secure enough for any practical purpose.
If one views the relative strengths of these two components in that way, then the unsoundness in the design becomes apparent.
When a pair of Quadibloc 2002 rounds are performed, the last 32 bits of each half of the block are modified in a way that is considered really secure. The first 32 bits are modified more prosaically. The middle 32 bits are left alone.
But before that happened, one half of the block was XORed with the other half, after going through what is considered a less secure transformation: the Quadibloc 2002A diffusion phase.
Not only do I not consider it to be as secure as a Quadibloc 2002 round, but it has the property that the enciphered version of a given byte of its input ends up in a different location on the output.
Thus, after the Quadibloc 2002 rounds, when we transform and XOR back in the other direction, information from that fourth subblock, in addition to being thoroughly enciphered on the one side, was also, in part, XORed with the middle two unenciphered subblocks on the other side, and is now being XORed back in again.
Although I had thought using the Quadibloc 2002A elements as an overall f-function would simply saturate the encipherment process with unpredictability, therefore, it appears as though it could provide a path by which information could leak through the Quadibloc 2002 rounds.
The overwhelming complexity of this cipher design may, in fact, provide some protection against this, but in other, simpler cipher designs, where a Feistel structure is superimposed on a manipulation between rounds that does not modify the entire block, this particular issue could be a genuine weakness.
There is also an argument that this leakage cannot be a real problem in a cipher of the type seen here, however. All the leaked information, when it makes the return journey to the half of the block it came from, is still going to be XORed into a subblock that either had gone through the strong transformation as the fourth subblock of a preceding Quadibloc 2002 round, or which will undergo the strong transformation as the fourth subblock of a succeeding Quadibloc 2002 round. The properties of block ciphers with a "ladder" architecture, particularly where an incomplete transformation (like a single round, rather than a pair of rounds, in a classical block cipher like DES) is performed in-line between rungs may be an interesting area of study.
Next
Start of Section
Skip to Next Chapter
Skip to Next Section
Table of Contents
Main Page