
This page is about codes and ciphers, which people use to communicate with each other in ways that other parties cannot (it is hoped) understand. Although secrecy in communication can precede literacy, for example by the use of obscure allusions, a spoken language that is different from the one commonly spoken, a jargon or cant of terms with special or secondary meanings, or a conventionalized way of speaking such as Pig Latin, the efflorescence of many and sophisticated methods of secret communications waited for the development of alphabetic writing, which allows any thought to be represented by a small number of easily manipulated characters.
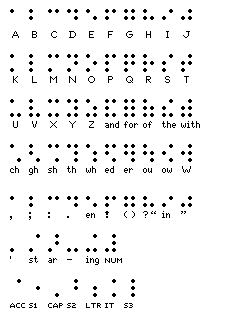
Even then, it took a conceptual breakthrough to realize that letters can be represented by other symbols; particularly in introductory books on the subject for children, this is often illustrated by various examples that are used today, such as Morse code, signal flags, Baudot, ASCII, or, as illustrated below, Braille and semaphore:


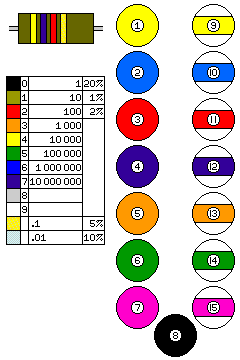
And, for another even more prosaic illustration, here is the color code used on resistors (as well as on the old mica capacitors) and the color code, if one can call it that, of pool balls:
One early and entertaining historical survey of the use of codes and ciphers was the book Secret and Urgent, by Fletcher Pratt, also the author of several novels. This book came out in the same year as Elementary Cryptanalysis, by Helen Fouché Gaines, which will be mentioned below. The title of this book is a particularly apt description of why methods of scrambling messages to keep them secret are used.
Obviously, if a message contains nothing that is confidential, there is no need to bother putting it into code or cipher.
But equally, if a message is not urgent, then even if it is secret, it can be communicated at some time when there is an opportunity to meet privately.
Only when both conditions exist: when the contents of a message must be kept secret, and yet the message is so urgent that the risk must be taken of sending it by a means that may allow others to read it, would people take the time and effort to put a message into cipher, and take the risk involved in relying on cipher to maintain its secrecy.
Of course, today computers carry out the steps involved in enormously complicated cipher schemes at the push of a button, so neither the effort nor the risk looms as large as it did during most of the history of the subject.
This site contains a brief outline of the various types of cipher systems that have been used historically, and tries to relate them to each other while avoiding a lot of mathematics.
The following books can be recommended for someone beginning to learn about the subject of secret writing:
The Codebreakers, David Kahn, Macmillan (1st ed.) Simon and Schuster (2nd ed.). This book is a fascinating history of cryptography, dealing with the role it has played in many historical events. There are also some nuggets of technical information not seen in other books aimed at the general public, and there is historical information about subjects related to secret codes, such as cable codes (which do not involve secrecy, and were for saving money on sending telegrams).
Elementary Cryptanalysis, Helen Fouché Gaines, Dover. Published under the title Cryptanalysis to avoid confusion with a book by Abraham Sinkov (also a good book), this book deals with pencil and paper ciphers, and is particularly aimed at people who solve such ciphers as a hobby. It describes a wide variety of ciphers and a multitude of solving methods.
And I will also mention two other books here:
Machine Cryptography and Modern Cryptanalysis, Cipher A. Deavours and Louis Kruh; Artech House. This book is a gold mine of information and was the source for much of what you will see in this web site about cipher machines of the rotor era. It is now out of print. Unfortunately, it was marred by a number of typographical errors. I had thought that regrettable, but felt that this was a common occurrence in books with a limited anticipated sale. An otherwise positive review in Cryptologia magazine (also a significant source, particularly for my account of the Siemens T-52) did include the comment that one might expect better than that, and as a result my faulty memory led me to categorize the review as "scathing", for which I apologize to its author (himself a significant source of information for my section on the Enigma's Uhr box), Frode Weierud. A number of the illustrations from this book were reprinted (with full permission, of course) in the more recent book Decrypted Secrets from Springer-Verlag.
Applied Cryptography, Bruce Schneier; John Wiley and Sons. This book is aimed at the computer professional who needs to implement secure systems involving cryptography. As it describes a wide selection of algorithms and protocols, it will be of interest to anyone concerned with cryptography in the computer era. This book is one of the most widely available books covering the subject matter, and it is frequently cited as a source and as an authority on the USENET newsgroup sci.crypt. The 2nd edition is considerably expanded, with fascinating detail on a much larger number of cipher systems.
Return to Home Page
Main Screen
Copyright (c) 1998, 1999, 2000 John J. G. Savard